A refined new Phishing-as-a-service technique, designated ‘CoPhish,’ is leveraging the capabilities of microsoft Copilot Studio to deceive users and pilfer sensitive login credentials. This emerging threat utilizes seemingly legitimate Microsoft domains to deliver fraudulent OAuth consent requests, making it significantly harder for individuals to discern malicious activity.
How CoPhish Works: A Deep dive
Table of Contents
- 1. How CoPhish Works: A Deep dive
- 2. Targeting Administrators and Circumventing Security Measures
- 3. The Attack in Action: From Phishing Email to Token Capture
- 4. Staying Ahead of Phishing Threats
- 5. frequently Asked Questions About CoPhish and OAuth Phishing
- 6. What specific vulnerabilities within Copilot Studio agents enable attackers to inject malicious prompts adn initiate unauthorized OAuth flows?
- 7. CoPhish Attack Exploits Copilot Studio Agents to Steal OAuth Tokens
- 8. Understanding the CoPhish Threat Landscape
- 9. How CoPhish works: A step-by-Step Breakdown
- 10. Targeted OAuth Providers & Potential Impact
- 11. Identifying Vulnerable Copilot Studio Agents
- 12. Mitigation Strategies: Protecting Your Organization
- 13. Real-World Examples & Case Studies (October 2024)
- 14. Benefits of Proactive Security Measures
Researchers at Datadog Security Labs initially identified the method, raising concerns about the inherent risks introduced by Copilot Studio’s flexible configuration options. The technique centers around creating customized chatbot workflows – known as “topics” – within Copilot Studio.These agents can be openly shared via a “demo website” feature hosted on a genuine Microsoft domain, immediately establishing an air of trustworthiness.
the core of the attack involves manipulating the “Login” topic, responsible for user authentication. Attackers can refine this topic to not only authenticate users but also redirect them to malicious URLs or request verification codes,all while appearing to be a standard Microsoft service.
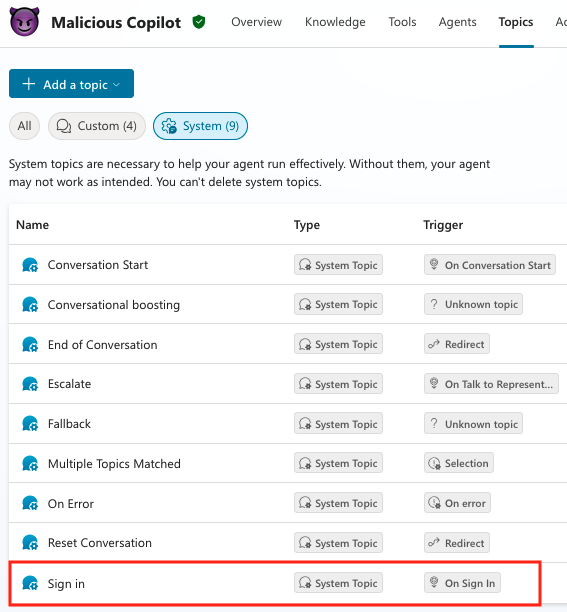
Targeting Administrators and Circumventing Security Measures
Katie Knowles, a Senior Security Researcher at Datadog, explains that attackers can utilize the Login button to deploy malicious applications, perhaps targeting even those without direct access to the core surroundings. While initial attacks focused on users with limited permissions,the risk extends to administrators. Currently, Microsoft’s security protocols limit the scope of attacks on standard users to OneNote access. However, external attackers can still target Application Administrators using externally registered applications, a loophole that remains unaddressed by current updates.
The attack sequence begins with the creation of a malicious application equipped with the configured sign-in topic, designed to capture session tokens via HTTP requests sent to a Burp Collaborator URL, embedding the access token within a ‘token’ header.The application ID,secret,and authentication provider URLs are crucial elements in setting up the agent’s sign-in parameters. Redirecting users to malicious URLs is a key component,with attackers exploiting the OAuth consent workflow to achieve their goals.

The Attack in Action: From Phishing Email to Token Capture
Attackers distribute these malicious agents via phishing emails or through platforms like Microsoft Teams. Due to the use of legitimate URLs and convincing page designs, users are easily tricked into believing they are interacting with a genuine Microsoft copilot service. A subtle indicator of malicious intent is the presence of the “Microsoft Power Platform” icon,which can be easily overlooked.
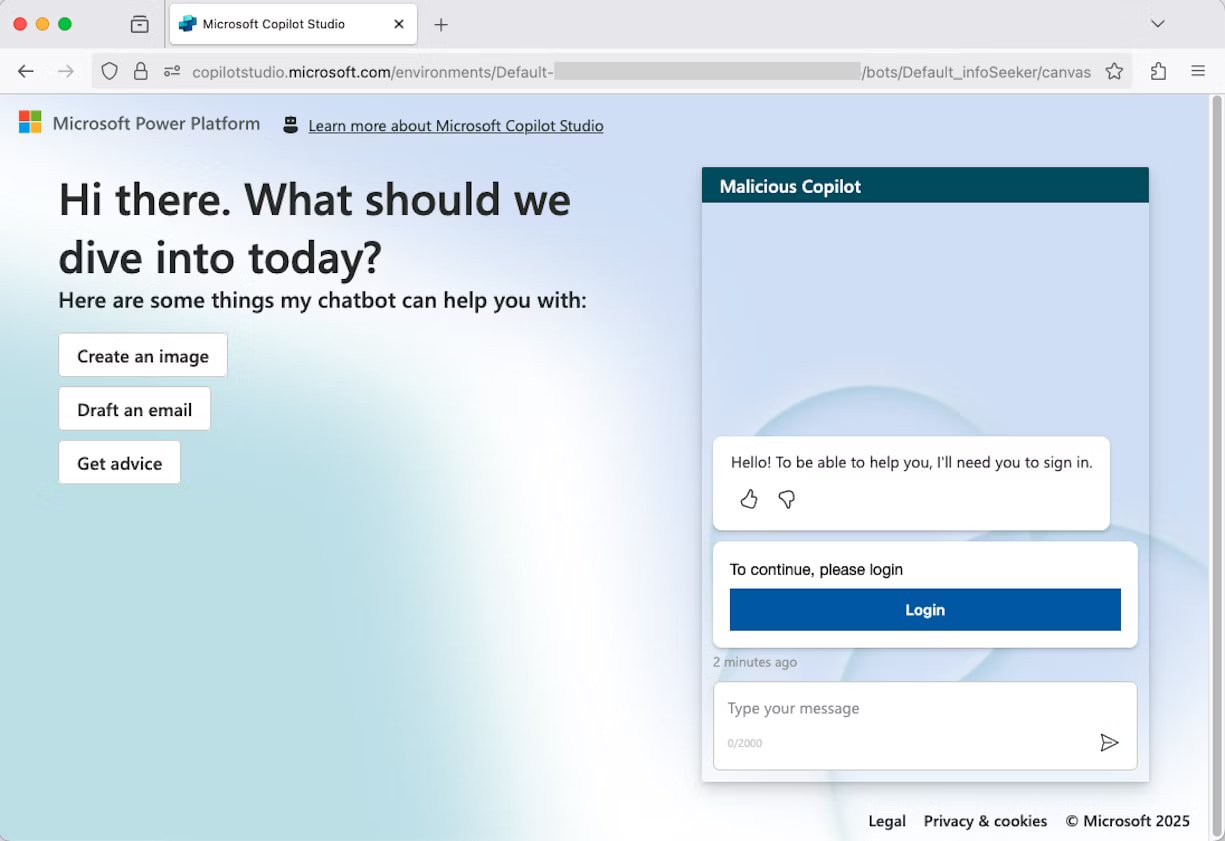
If an administrator falls victim to the scheme and approves the malicious app’s permissions, they are redirected to a standard OAuth URL ([token.botframework.com]) to validate the bot connection. Although seemingly routine, this process results in the user’s session token being silently forwarded to the attacker and their session being compromised, all while the connection appears to originate from Microsoft’s trusted IP addresses, masking the malicious activity from standard network monitoring.
Here’s a breakdown of the cophish attack workflow:
.jpg)
Microsoft has acknowledged the issue and has pledged to address the underlying vulnerabilities in a forthcoming software update. A spokesperson stated, “we’ve investigated this report and are taking action to address it through future product updates. While this technique relies on social engineering, we remain committed to hardening our governance and consent experiences and are evaluating additional safeguards to help organizations prevent misuse.”
| Vulnerability | Description | Mitigation |
|---|---|---|
| CoPhish Technique | Exploitation of microsoft Copilot Studio for credential theft. | Limit administrative privileges, reduce application permissions. |
| OAuth Redirection | Malicious redirection after successful login. | Implement strong application consent policies. |
| Admin Vulnerability | Targeting of administrators with externally registered applications. | Disable user application creation defaults; monitor application consent. |
Staying Ahead of Phishing Threats
Phishing attacks are continuously evolving. According to the Anti-Phishing Working Group (APWG), phishing attacks increased by 47% in the first half of 2024 compared to the same period in 2023, highlighting the growing sophistication of these threats. Organizations must prioritize employee training, implement multi-factor authentication (MFA), and regularly review security protocols to mitigate the risk of falling victim to such attacks.
Did You Know? Approximately 90% of data breaches involve a human element, frequently enough stemming from successful phishing attacks.
Pro Tip: Always scrutinize URLs before entering your credentials, and be wary of unexpected requests for sensitive facts.
Do you have a robust incident response plan in place to address potential phishing attacks? What steps is your association taking to educate employees on identifying and reporting suspicious activity?
frequently Asked Questions About CoPhish and OAuth Phishing
- what is CoPhish? CoPhish is a new phishing technique that leverages Microsoft Copilot Studio to steal user credentials.
- How does CoPhish exploit OAuth? It utilizes fraudulent OAuth consent requests delivered through legitimate Microsoft domains.
- Who is moast at risk from CoPhish? Administrators with elevated privileges are notably vulnerable.
- Is Microsoft addressing the CoPhish vulnerability? Yes, Microsoft has acknowledged the issue and plans to release a fix in a future update.
- What can organizations do to protect themselves from CoPhish? Organizations should limit admin privileges, reduce app permissions, and enforce governance policies.
- What is OAuth and why is it a target for phishers? OAuth is an authentication protocol that allows third-party applications to access user data; compromised OAuth tokens can grant attackers broad access.
- How can I identify a potential CoPhish attack? Look for the “Microsoft Power Platform” icon and be cautious of unexpected login requests.
Share this critical information with your network to raise awareness about the evolving threat landscape and empower individuals and organizations to defend against phishing attacks.
CoPhish Attack Exploits Copilot Studio Agents to Steal OAuth Tokens
Understanding the CoPhish Threat Landscape
The cybersecurity landscape is constantly evolving, and a recent threat dubbed “CoPhish” highlights a novel attack vector targeting Microsoft Copilot Studio agents. this sophisticated phishing campaign leverages the power of generative AI to automate and scale OAuth token theft, posing a meaningful risk to organizations relying on these agents for customer interaction and automation. Understanding how CoPhish operates is crucial for implementing effective mitigation strategies. OAuth token theft, AI-powered phishing, and Copilot Studio security are key terms to grasp when addressing this emerging threat.
How CoPhish works: A step-by-Step Breakdown
CoPhish doesn’t rely on traditional phishing emails. rather, it exploits vulnerabilities within Copilot Studio agents – conversational AI bots used for tasks like customer support, lead generation, and internal workflows. here’s a detailed look at the attack chain:
- Agent Compromise: Attackers identify publicly accessible Copilot studio agents. Frequently enough, these agents are configured with broad permissions to access various APIs and services.
- Malicious Prompt Injection: The attacker crafts a carefully designed prompt that manipulates the agent into initiating an OAuth 2.0 authorization flow. This prompt tricks the agent into believing it needs to access a resource on behalf of a legitimate user.
- OAuth Redirection & Token Capture: The authorization flow redirects the user to a malicious website controlled by the attacker, disguised as a legitimate Microsoft login page. Users unknowingly enter their credentials, granting the attacker an OAuth access token.
- Token Exploitation: The stolen access token allows the attacker to impersonate the user and access resources the user is authorized to access, including sensitive data and systems. This can lead to data breaches, account takeover, and further lateral movement within the organization. API access, data exfiltration, and account compromise are all potential outcomes.
Targeted OAuth Providers & Potential Impact
CoPhish isn’t limited to a single OAuth provider. Researchers have observed attacks targeting:
* Microsoft 365: Compromising Microsoft 365 accounts grants access to email, documents, and other critical business data.
* Salesforce: Access to Salesforce data can expose valuable customer data and sales pipelines.
* Google Workspace: Compromised Google Workspace accounts can lead to data breaches and disruption of business operations.
* ServiceNow: Access to ServiceNow can expose IT service management data and perhaps disrupt critical IT processes.
The impact of a successful CoPhish attack can be severe, ranging from financial losses and reputational damage to legal liabilities and regulatory fines. Data security incidents, reputational risk, and compliance violations are all serious concerns.
Identifying Vulnerable Copilot Studio Agents
Proactive identification of vulnerable agents is paramount. Consider these factors:
* Public Accessibility: Agents accessible without authentication are prime targets.
* Broad Permissions: Agents with excessive permissions to access APIs and services are more susceptible. Implement the principle of least privilege.
* Unvalidated Input: Agents that don’t properly validate user input are vulnerable to prompt injection attacks.
* Lack of Monitoring: Insufficient monitoring and logging make it difficult to detect malicious activity. Security Information and Event Management (SIEM) systems are crucial.
Mitigation Strategies: Protecting Your Organization
Several steps can be taken to mitigate the risk of CoPhish attacks:
- Restrict Agent Accessibility: Limit access to Copilot Studio agents to authorized users onyl. Implement strong authentication mechanisms.
- Implement Least Privilege: Grant agents only the minimum necessary permissions to perform their tasks. Regularly review and refine these permissions.
- Input Validation & Sanitization: Implement robust input validation and sanitization techniques to prevent prompt injection attacks. Filter out potentially malicious characters and commands.
- Monitor Agent Activity: Implement extensive monitoring and logging to detect suspicious activity.Look for unusual API calls, unauthorized access attempts, and unexpected behavior.
- User Awareness Training: Educate users about the risks of phishing and social engineering attacks. Emphasize the importance of verifying the legitimacy of websites before entering credentials. Phishing simulations can be highly effective.
- Regular Security Audits: Conduct regular security audits of Copilot studio agents to identify and address vulnerabilities.
- enable Conditional Access policies: Leverage Microsoft’s Conditional Access policies to enforce multi-factor authentication and restrict access based on location, device, and other factors.
Real-World Examples & Case Studies (October 2024)
In October 2024, a financial services firm experienced a CoPhish attack targeting a customer support Copilot Studio agent. The attacker successfully stole an OAuth token,gaining access to customer account information.The incident resulted in a data breach affecting over 10,000 customers and significant financial losses for the firm. This case highlights the real-world consequences of neglecting Copilot Studio security. Another incident involved a healthcare provider where an attacker used a compromised agent to access patient data, leading to a HIPAA violation and a substantial fine.
Benefits of Proactive Security Measures
Investing in proactive security measures to protect against cophish attacks offers numerous benefits:
* Reduced Risk of data Breaches:
