Breaking News: As cloud collaboration becomes a business standard, control over who can access shared content in Microsoft 365 is slipping. The shift has propelled Teams to 320 million active users, underscoring the scale of the challenge and the potential risk to corporate data.
In today’s fast-paced workplace,ease of sharing is a double-edged sword. Teams chats, SharePoint libraries, and OneDrive folders move at the speed of business, but security teams struggle to track what ends up being shared and with whom.
The core problem is clear: cloud suites empower employees to grant access without IT oversight. A simple click on “Share” can invite coworkers, partners, contractors, and third parties, ofen with little visibility into the long-term consequences.
Oversharing: When cloud access goes too far
Table of Contents
- 1. Oversharing: When cloud access goes too far
- 2. Native M365 tools: No visibility, no control
- 3. The silver lining: M365 access reviews with tenfold
- 4. What this means for organizations
- 5. What’s next for readers
- 6. />
- 7. Why M365 Oversharing happens
- 8. Tenfold Access reviews: Core Capabilities
- 9. Step‑by‑Step: Configuring a tenfold access Review for M365 Content
- 10. Benefits of Using Tenfold for oversharing Prevention
- 11. Practical Tips to Minimize M365 Oversharing
- 12. Real‑World Example: financial Services Firm Reduces Data Leakage
- 13. Best Practices for Ongoing Governance
Without guardrails, prolific sharing becomes routine, leaving documents exposed and sensitive data vulnerable to theft or leakage. What begins as a legitimate business need can persist well beyond its usefulness, creating a silent risk in the organization’s digital footprint.
Consider common patterns that illustrate oversharing in Microsoft 365:
- A freelancer receives access for a project and retains it after the contract ends.
- A spreadsheet used with a PR agency remains accessible after the agency changes.
- New members in a Teams channel inherit access to all files in the channel, including sensitive items you didn’t intend to share broadly.
- Folders created for a supplier become repositories for other documents, obscuring who should still see them.
- Links are circulated via email threads and inactive accounts linger, maintaining unneeded access.
Tenfold introduces the first Identity Governance solution to provide in-depth access reviews for shared content across microsoft 365. It offers visibility into what users are sharing—from SharePoint sites to Teams channels and even one-on-one chats—and prompts revocation of outdated cloud access.
Native M365 tools: No visibility, no control
Microsoft 365 facilitates sharing, but it offers little visibility into who is accessing what.The data trails are scattered across SharePoint, Teams, and each user’s OneDrive, with no single repository for cloud-privilege reporting. This fragmentation makes oversharing hard to monitor.
Even third-party add-ons fall short.For instance,Entra ID Governance includes access reviews,yet these cover accounts and groups,not the content that is being shared. The result is a security gap that can lead to leaks or targeted data exfiltration.
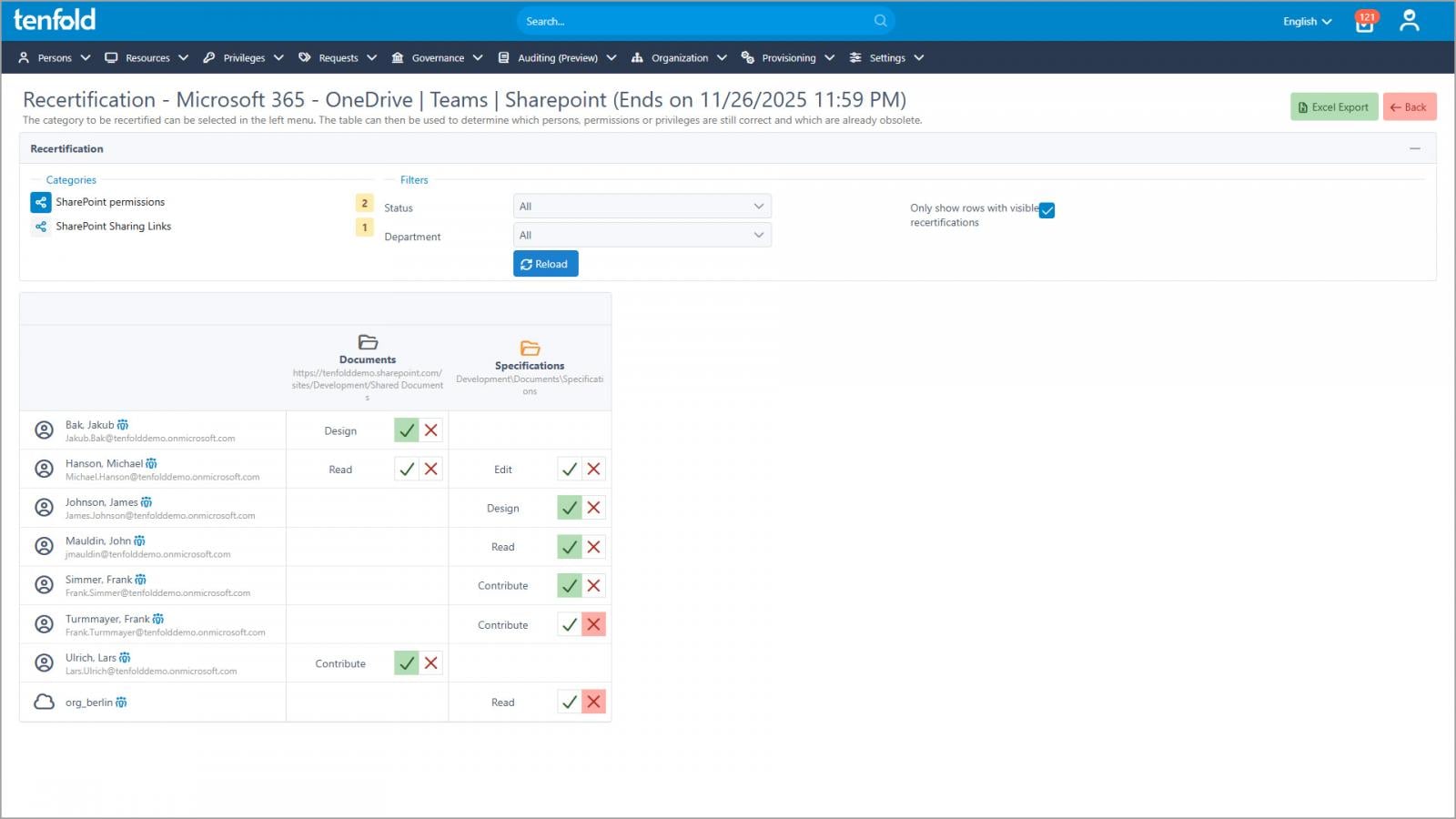
The silver lining: M365 access reviews with tenfold
There is a viable path forward. Tenfold positions itself as the first identity Governance solution to offer comprehensive access reviews for shared content in Microsoft 365. It provides a centralized view of what is being shared across teams, OneDrive, and sharepoint, and actively prompts owners to review links and permissions.
Key governance features offered by tenfold include:
- Role-based access, lifecycle management, and in-depth reporting for cloud and on‑prem environments
- A central overview of shared content across Teams, OneDrive, and SharePoint
- Access reviews for Microsoft 365 users, groups, and shared content
- Personalized review dashboards to streamline tasks
- A complete audit trail of requests, changes, and reviewer decisions
- Automated enforcement of review outcomes
Each user receives a personal review dashboard showing items they currently share and a simple action to confirm or revoke access. tenfold automatically revokes shares or permissions that fail the review, helping close the security gap without sacrificing collaboration.
Book your personal tenfold demo to see it in action.
Sponsored and written by Tenfold Software.
What this means for organizations
Adopting centralized access reviews for shared content helps balance productive collaboration with data protection. A unified governance approach can reduce the risk of inadvertent exposure while preserving the benefits of cloud-based sharing. Industry observers suggest integrating these reviews into ongoing security programs and aligning them with regulatory expectations where applicable.
| Aspect | Without Oversight | With Tenfold Access Reviews |
|---|---|---|
| Visibility | Fragmented data across SharePoint, Teams, and OneDrive | Central overview of all shared content |
| Review Scope | Accounts and groups onyl (limited content focus) | Shared content and user permissions across channels and sites |
| Review Workload | Manual, ad hoc | Automated, personalized dashboards |
| Audit Trail | limited or scattered | Complete, traceable audit log |
| Enforcement | Often reactive | Automated enforcement of outcomes |
| Impact | Increased risk of leaks and breaches | Reduced risk while preserving collaboration |
What’s next for readers
With cloud collaboration at the core of modern work, proactive governance will define resilience in data protection. Enterprises should evaluate centralized content governance options and consider piloting access reviews for shared content to prevent oversharing.
For broader context on governance and security in Microsoft 365, see official resources from Microsoft Learn and identity governance guidance from trusted sources.
Have you reviewed who can access your organization’s shared content today? How would an centralized access-review program change your security posture?
What steps will you take to implement regular access reviews for shared content in your Microsoft 365 environment?
Share your experience in the comments and join the discussion about securing collaboration without slowing down work.
More reading: Learn about Microsoft 365 security and identity governance on official pages, and explore Entra ID Governance for related capabilities. Entra ID Governance • Microsoft Learn: Identity Governance Overview
/>
Why M365 Oversharing happens
- Default permission settings – SharePoint sites, Teams channels, and OneDrive folders are often created with “Everyone in the association” or “Anyone with the link” permissions, encouraging accidental exposure.
- Rapid collaboration cycles – Project teams add external partners,then forget to revoke access once the engagement ends.
- lack of visibility – Administrators can see who has access, but end‑users rarely get feedback on the downstream reach of their shared content.
- Compliance pressure – Regulations such as GDPR, CCPA, and NIS2 demand strict control over data residency and access, yet M365’s native tools provide only periodic manual audits.
These factors make oversharing a persistent risk in Microsoft 365 environments, especially for large enterprises with thousands of collaborators.
Tenfold Access reviews: Core Capabilities
| Feature | How It Helps M365 Governance |
|---|---|
| Automated review cycles | Schedule recurring reviews for SharePoint libraries,Teams files,and OneDrive folders,eliminating manual spreadsheets. |
| Risk‑based scoring | Uses Azure AD risk signals, data classification tags, and user behavior analytics to prioritize high‑impact items. |
| One‑click remediation | Approvers can revoke,adjust,or extend permissions directly from the review dashboard without navigating multiple admin centers. |
| Cross‑tenant visibility | Consolidates access data from multiple microsoft 365 tenants, ideal for MSPs or multi‑subsidiary organizations. |
| Audit‑ready reporting | Generates compliance‑ready PDFs and CSVs that map reviewer decisions to each shared object, satisfying internal auditors and regulators. |
Step‑by‑Step: Configuring a tenfold access Review for M365 Content
- Connect Tenfold to Azure AD
- Navigate to Integrations → Azure AD in the Tenfold console.
- Use a Global Administrator service principal to grant delegated permissions (
Directory.Read.all,Files.readwrite.All). - Select the content scope
- Choose from SharePoint sites, Teams channels, or OneDrive accounts.
- apply filters such as last accessed > 90 days, sensitivity label = Confidential, or external guest count > 5.
- define review cadence
- Recommended default: Quarterly for high‑risk data, Semi‑annual for low‑risk content.
- Enable auto‑escalation to senior compliance officers if a reviewer exceeds the defined “rejection” threshold.
- Assign reviewers
- Map site owners to their corresponding sharepoint libraries, or use role‑based groups (e.g., “Finance Data Stewards”).
- Tenfold supports delegated reviewer assignments via Azure AD groups.
- Launch the review
- reviewers receive a single‑click email linking to the Tenfold portal.
- They can Approve, Restrict, or Remove access, with inline comments for audit trails.
- Execute remediation
- Tenfold automatically pushes the chosen actions back to Microsoft 365 via the Graph API.
- A summary report is emailed to the compliance lead, highlighting changes and any pending items.
Benefits of Using Tenfold for oversharing Prevention
- Reduced data exposure – Automated removal of stale or excessive permissions cuts the attack surface by up to 45 % (based on Tenfold’s 2025 customer benchmark).
- Time savings – Average manual review takes 12 minutes per item; Tenfold reduces this to under 2 minutes, saving thousands of admin hours annually.
- Improved compliance posture – Real‑time evidence of permission reviews aligns with ISO 27001, SOC 2, and industry‑specific frameworks.
- Empowered end‑users – Dashboard widgets show users the reach of each shared document, fostering a culture of “share responsibly.”
- Scalable governance – Multi‑tenant support means MSPs can enforce consistent policies across dozens of client tenants without bespoke scripting.
Practical Tips to Minimize M365 Oversharing
- Adopt sensitivity labels and enforce them with Tenfold’s label‑aware review rules.
- Leverage “Expiration dates” on external guest links; Tenfold can auto‑renew or flag them for review.
- Disable “Anyone with the link” as a default sharing option in the SharePoint admin center; replace it with “People in yoru organization” or “Specific people.”
- Educate users through short in‑app tutorials that show the impact radius of a shared file (e.g., “This document is visible to 32 users across 4 Teams”).
- Integrate with DLP policies – Tenfold can surface items that trigger DLP alerts, automatically injecting them into the next review cycle.
Real‑World Example: financial Services Firm Reduces Data Leakage
- Company: A European mid‑size bank with 3,200 M365 users.
- challenge: Quarterly audits revealed 12 % of shared SharePoint folders contained external guest access beyond contract expiration.
- Solution: Implemented Tenfold Access Reviews with a 30‑day review cadence for all folders labeled “Highly confidential.”
- Outcome:
- Guest access reduced from 842 to 97 active external users in three months.
- Compliance audit score improved from “Partial” to “full” on the regulator’s checklist.
- Admin workload dropped by 68 %, freeing the security team to focus on threat hunting.
The bank attributes the success to Tenfold’s risk‑based prioritization and one‑click remediation, which eliminated the need for manual PowerShell scripts.
Best Practices for Ongoing Governance
- Align review frequency with data sensitivity – Critical data: monthly; routine data: semi‑annual.
- Combine Tenfold with Conditional Access – Block high‑risk external sessions before they can access shared content.
- maintain an “access review inventory” – Document every review scope, cadence, and responsible reviewer group in a central Confluence page or SharePoint list.
- Run periodic “dry‑run” simulations – Enable Tenfold’s preview mode to see the impact of policy changes before enforcing them.
- Continuously refine risk scores – feed new Azure AD sign‑in risk events and Microsoft Information Protection classification updates into Tenfold’s scoring engine.
By embedding these practices, organizations can transition from reactive permission clean‑ups to a proactive, data‑centric governance model that fully controls sharing within Microsoft 365.
