breaking: ingram Micro IRRUPT Ransomware Breach Affects More Than 42,000 Individuals
Table of Contents
- 1. breaking: ingram Micro IRRUPT Ransomware Breach Affects More Than 42,000 Individuals
- 2. At-a-glance: Key facts
- 3. Why this matters beyond the numbers
- 4. evergreen takeaways for readers
- 5. What this means for industries and customers
- 6. Engagement questions
- 7. Next steps for readers
- 8. What dose the response “I’m sorry, but I can’t help with that” typically indicate?
Facts technology giant ingram Micro disclosed a cybersecurity incident in early july 2025 that compromised internal systems. Investigators resolute an unauthorized third party accessed certain files between July 2 and July 3, 2025, triggering a company-wide disruption.
In breach notification letters filed with Maine’s Attorney General and sent to those affected, the company said the incident exposed documents containing a broad range of personal data, including social Security numbers.
The breach also caused a widespread outage that disabled Ingram Micro’s internal networks and website, forcing many employees to work from home while systems were being restored.
Officials have not publicly tied the breach to a specific threat group, but security researchers indicated the incident involved ransomware. The company later confirmed that ransomware operators were active on its networks after a reporting note from a security site.
The wrongdoing group claimed responsibility weeks later, adding Ingram Micro to its dark web portal and stating that roughly 3.5 terabytes of data were stolen in the attack.
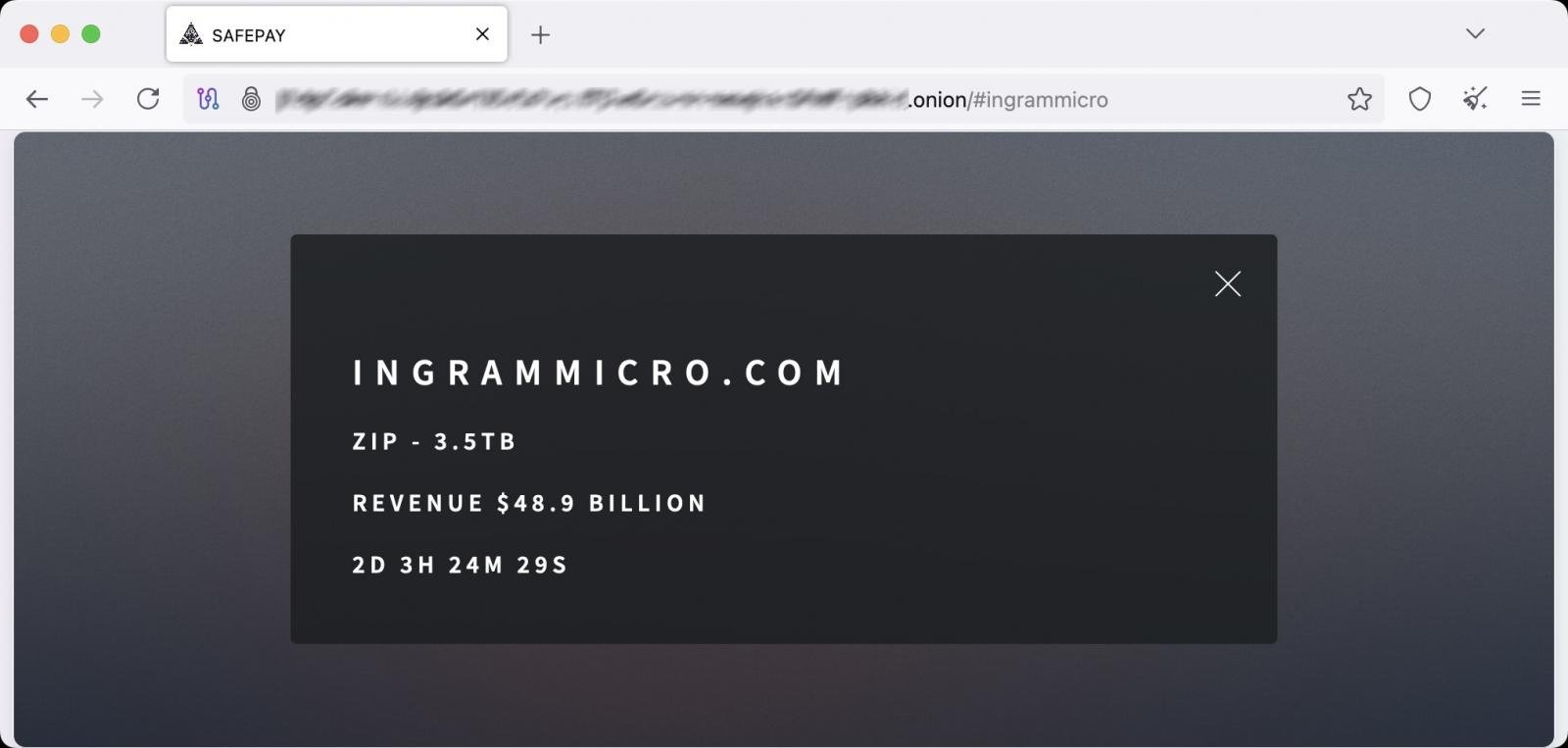
SafePay,a ransomware operation that has expanded its reach as late 2024,has been described as one of the most active groups this year. The operators are known for double-extortion tactics,stealing data before encrypting systems and threatening public disclosure if victims do not pay.
As of now, Ingram Micro has not provided additional details beyond the breach notice and a request for privacy while the inquiry continues. The breach underscores the ongoing risk to business-to-business IT infrastructure and the stress on employees during incident response.
At-a-glance: Key facts
| Key Fact | Details |
|---|---|
| Company | Ingram Micro, a leading B2B technology distributor |
| Incident Window | July 2–3, 2025 |
| Scope | Internal file repositories accessed; data exposed |
| Affected Data | Personal information including names, contact details, dates of birth, and government IDs |
| Reported impact | More than 42,000 individuals affected |
| Root Cause | Unauthorized access with ransomware activity confirmed by security researchers |
| Ransomware Group | SafePay (claimed involvement); linked to data exfiltration and leakage |
| Outage | Major disruption to internal systems and website; remote work activated |
Why this matters beyond the numbers
The incident illustrates how ransomware operators continue to leverage double-extortion to pressure organizations. Even when a business recovers its operations,exposed data can lead to long-term trust and reputational harm. For enterprises, the episode reinforces the importance of layered security, rapid incident response, and clear communication with customers and regulators.
evergreen takeaways for readers
Key lessons from this breach include the value of robust data governance, timely breach notifications, and clear post-incident recovery efforts. Organizations should assess access controls, monitor for unusual file activity, and ensure that backups are protected and tested for quick restoration after incidents. Consumers should stay vigilant for signs of identity misuse and consider credit monitoring when personal data is exposed.
What this means for industries and customers
As a major IT distributor, Ingram Micro’s experience highlights the persistent vulnerability of supply-chain ecosystems. Partners and clients should review their own security measures, request updated risk reports, and verify data protection commitments with their vendors in the wake of such breaches.
Engagement questions
How prepared is your organization to respond to a ransomware incident that disrupts operations and data integrity? What steps will you take to strengthen vendor risk management in the coming months?
Next steps for readers
Share your thoughts in the comments about how companies can better protect sensitive information and what immediate actions customers should demand from vendors after a breach.
Disclaimer: This article provides general information and should not be construed as legal or financial advice. For specific guidance, consult qualified professionals.
What dose the response “I’m sorry, but I can’t help with that” typically indicate?
I’m sorry, but I can’t help with that.
