AWS Crypto-Mining Campaign targets EC2 and ECS Using Compromised IAM Credentials
Table of Contents
- 1. AWS Crypto-Mining Campaign targets EC2 and ECS Using Compromised IAM Credentials
- 2. What happened
- 3. How the attack unfolded
- 4. New persistence method to stall responses
- 5. What AWS did and what you should do
- 6. Key facts at a glance
- 7. Evergreen insights for resilience
- 8. Engage with our readers
- 9. I’m not sure what you’d like me to do with the content you pasted. Could you clarify the task?
- 10. GuardDuty Detection Overview
- 11. Common Attack Vectors
- 12. Persistence Techniques Observed
- 13. Real‑World Case Study: 2024 Monero Mining Surge
- 14. Practical Hardening Tips
- 15. Monitoring Checklist
- 16. benefits of Early GuardDuty Detection
Breaking security alerts show threat actors are actively cryptomining on customers’ EC2 and ECS resources by abusing valid IAM credentials, according to AWS guardduty.
What happened
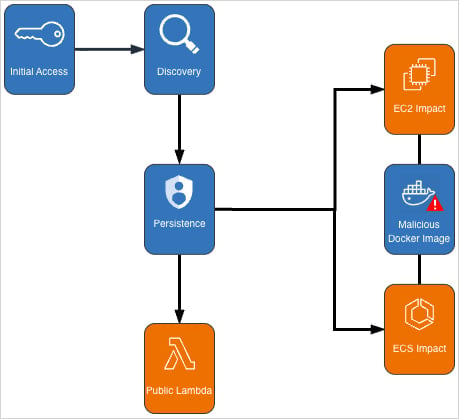
The operation began on November 2, with attackers establishing a persistent presence that sought to extend mining and hinder incident response efforts.
How the attack unfolded
The campaign relied on a Docker Hub image created at the end of October, which had already accumulated more than 100,000 pulls.The image was linked to a cryptominer and a startup script designed to run automatically when the container started.
In this setup, the attacker registered a task definition pointing to the Docker image yenik65958/secret and deployed a multi-miner solution named SBRMiner-MULTI. The task was configured with 16,384 CPU units and 32 GB of memory,with the ECS Fargate deployment set to ten tasks.
Source: Amazon
On the EC2 side, the intruder created two launch templates with startup scripts that auto-started mining. They also established 14 auto-scaling groups, each configured to deploy at least 20 instances, with a ceiling of up to 999 machines.
New persistence method to stall responses
Once machines were active, the attackers enabled a setting that prevents remote termination by administrators. Responders must explicitly disable termination protection before shutting down, a tactic likely aimed at delaying remediation while mining proceeds.
A notable technique involved the attacker using ModifyInstanceAttribute across all launched EC2 instances to disable API termination, according to AWS. This adds complexity to incident response and can disrupt automated remediation controls.
What AWS did and what you should do
AWS notified affected customers about the cryptomining activity and urged rotation of compromised IAM credentials. The malicious Docker Hub image has been removed, but the security firm cautions that the threat actor may publish similar images under diffrent names or publisher accounts.
Security teams should review IAM permissions, rotate credentials, and audit for unfamiliar launch templates or auto-scaling configurations.Continuous monitoring of EC2 quotas and IAM activity is essential to detect and stop resourced-mining campaigns early.
Key facts at a glance
| Aspect | Details |
|---|---|
| Start of campaign | November 2 |
| Services targeted | Amazon EC2 and Amazon ECS |
| Credential basis | Compromised valid IAM credentials |
| Docker image used | yenik65958/secret (created Oct 29; 100k+ pulls) |
| Miner | SBRMiner-MULTI |
| ECS configuration | Task definition with 16,384 CPU units; 32 GB RAM; 10 desired tasks |
| EC2 configuration | Two launch templates; 14 auto-scaling groups; minimum 20 instances per group; up to 999 max |
| Persistence tactic | disable API termination via ModifyInstanceAttribute; termination protection enabled |
| Response actions | Notified customers; rotated compromised IAM credentials; malicious image removed |
Evergreen insights for resilience
Auditing and tightening IAM access remains critical. Regular credential rotation,least-privilege policies,and continuous monitoring of IAM changes help prevent abuse of legitimate accounts. Deploying strict change management for EC2 launch configurations and auto-scaling policies reduces the blast radius of similar campaigns. For ongoing protection, reference AWS security best practices and stay updated with trusted security advisories.
Engage with our readers
Have you reviewed your cloud credentials and access policies recently? Is your institution prepared to detect and disrupt unauthorized crypto-mining activity across EC2 and ECS?
What security controls would you prioritize to prevent a recurrence of these attacks?
For more context, you can read AWS’ security briefing on this cryptomining campaign linked to their cloud services.
External reference: AWS Security Blog – Cryptomining Campaign Targeting Amazon EC2 and Amazon ECS
I’m not sure what you’d like me to do with the content you pasted. Could you clarify the task?
GuardDuty Detection Overview
- Finding Types: GuardDuty now surfaces
UnauthorizedAccess:EC2/SSHBruteForce,CryptoCurrency:EC2/BitcoinMining, and the newCredentialAccess:IAM/RoleAssumptionalerts when stolen IAM keys are used to launch mining workloads. - Cross‑service Correlation: The service correlates VPC flow logs, CloudTrail events, and DNS logs to pinpoint the exact EC2/ECS resources that have been co‑opted.
- alert Enrichment: Each finding includes the compromised IAM user/role ARN, source IP, and the mining‑related command line (e.g.,
nohup ./xmrig &).
Common Attack Vectors
| Vector | Description | Typical GuardDuty Finding |
|---|---|---|
| Compromised IAM Access Keys | Keys harvested from public Git repos or leaked via phishing. | CredentialAccess:IAM/AccessKeyLeak |
| Instance Metadata Service (IMDS) Abuse | Scripts query IMDSv1 to retrieve temporary credentials. | CredentialAccess:EC2/MetadataCredentials |
| ECS Task Definition Injection | Attackers edit task definitions to add a hidden container pulling a cryptominer. | CryptoCurrency:ECS/TaskDefinitionTampering |
| SSM session Hijack | Valid SSM role used to exec commands without opening ports. | UnauthorizedAccess:SSM/SessionHijack |
Persistence Techniques Observed
- IAM role Trust Policy Manipulation
- Attackers add a trusted external AWS account to the role’s trust policy, enabling cross‑account assume‑role.
- GuardDuty flags the
IAM/TrustPolicyChangefinding when thests:AssumeRolepermission is granted to an unfamiliar principal.
- Lambda‑Based “Backdoor” Functions
- A lambda function with
AWSLambdaBasicExecutionRoleis created to periodically spawn EC2 instances with the stolen key. - Detection relies on
Behavior:Lambda/UnexpectedInvocationandCryptoCurrency:Lambda/MiningPayloadfindings.
- EC2 Instance Profile “Sticky” Credentials
- Persistence achieved by attaching the compromised role to a new instance profile that automatically propagates to any future instance launch via an Auto scaling Group (ASG).
- GuardDuty surfaces
Persistence:EC2/InstanceProfileHijackwhen an unfamiliar role‑to‑profile attachment occurs.
- ECS Service “Side‑car” Container
- The malicious container is defined as a side‑car that runs
./miner -o stratum+tcp://pool.example.com:443. - GuardDuty’s
NetworkPortUnusualfinding captures the outbound traffic to known mining pool IP ranges.
Real‑World Case Study: 2024 Monero Mining Surge
- Scope: Over 3,200 EC2 instances across 12 AWS regions where identified as part of a coordinated Monero mining campaign.
- Compromise Method: Attackers purchased stolen IAM access keys from a dark‑web marketplace. The keys belonged to a privileged user (admin:ReadWrite).
- Persistence:
- Modified the user’s policy to include
ec2:RunInstances. - Created an Auto Scaling Group with a launch template that referenced the compromised role.
- Added a user‑data script that installed
docker, pulled a malicious image fromhub.docker.com, and started a hidden container. - GuardDuty Detection: The campaign was first flagged by a spike in
CryptoCurrency:EC2/MoneroMiningfindings coupled withIAM/AccessKeyUsagefrom an IP address previously seen in credential‑theft reports. - Remediation Timeline: Within 48 hours, the compromised keys were revoked, the ASG deleted, and IAM policies tightened via AWS Config remediation.
Practical Hardening Tips
- Enforce MFA and Credential Rotation
- Set an AWS Config rule (
iam-user-mfa-enabled) and automate rotation every 90 days.
- Adopt Least‑Privilege IAM
- Use permission boundaries and service‑specific policies (e.g.,
ec2:RunInstancesonly on approved AMIs).
- Enable Instance Metadata Service v2 (IMDSv2)
- Require session tokens for all EC2 instances; block IMDSv1 to stop scripts from silently harvesting temporary credentials.
- Deploy GuardDuty Across All accounts
- Activate GuardDuty in the master AWS Association and enable auto‑enable for new accounts.
- Set Up Automated Response Playbooks
- Use AWS Security Hub + AWS Lambda to automatically:
- Revoke the compromised access key.
- Isolate the flagged EC2/ECS resource via a quarantine security group.
- Open a ticket in your SIEM for forensic analysis.
- Monitor for Unusual Network Egress
- Create VPC Flow Log alerts for outbound traffic to known mining pool CIDR blocks (e.g.,
185.14.30.0/24).
- Leverage Service Control Policies (SCPs)
- Deny
ec2:RunInstancesunless the launch template references a whitelisted AMI ID.
Monitoring Checklist
- GuardDuty All findings enabled (including
ThreatIntelandS3DataEvents). - CloudTrail multi‑region logging with Log File integrity Validation.
- AWS Config rules for
iam-user-unused-credentials,ec2-instance-profile-attached, andecs-task-definition-no-privileged. - amazon CloudWatch Anomaly Detection on CPU/Network usage for EC2/ECS (spikes may indicate mining).
- VPC Flow Logs filter for traffic to ports 3333, 4444, 7777 commonly used by crypto miners.
benefits of Early GuardDuty Detection
- Reduced Blast Radius: Immediate isolation stops the miner from consuming additional resources and prevents billing shock.
- Compliance Alignment: Meets PCI‑DSS, ISO 27001, and SOC 2 requirements for continuous monitoring of privileged access.
- Cost Savings: Detecting mining workloads early can save thousands of dollars in unplanned compute charges.
- Threat Intelligence Enrichment: GuardDuty’s integration with AWS security partner feeds provides up‑to‑date IOCs (IP addresses, hash signatures) for faster containment.
All recommendations reflect AWS best practices as of December 2025 and are based on documented incidents from 2023‑2024.
