technology to deliver malware, with North Korean-backed hackers among those utilizing the technique.">
News">
New ‘EtherHiding’ Technique Enables malware Delivery Via Blockchain
Published: 2025-10-20
A elegant and evolving cybersecurity threat, now known as “EtherHiding,” is enabling malicious actors to conceal and deliver malware using the decentralized infrastructure of blockchain technology. Recent investigations reveal that hackers are exploiting the openness of platforms like Ethereum and the BNB Smart Chain to store and distribute harmful code, marking a novel approach to cyberattacks.
How EtherHiding Works
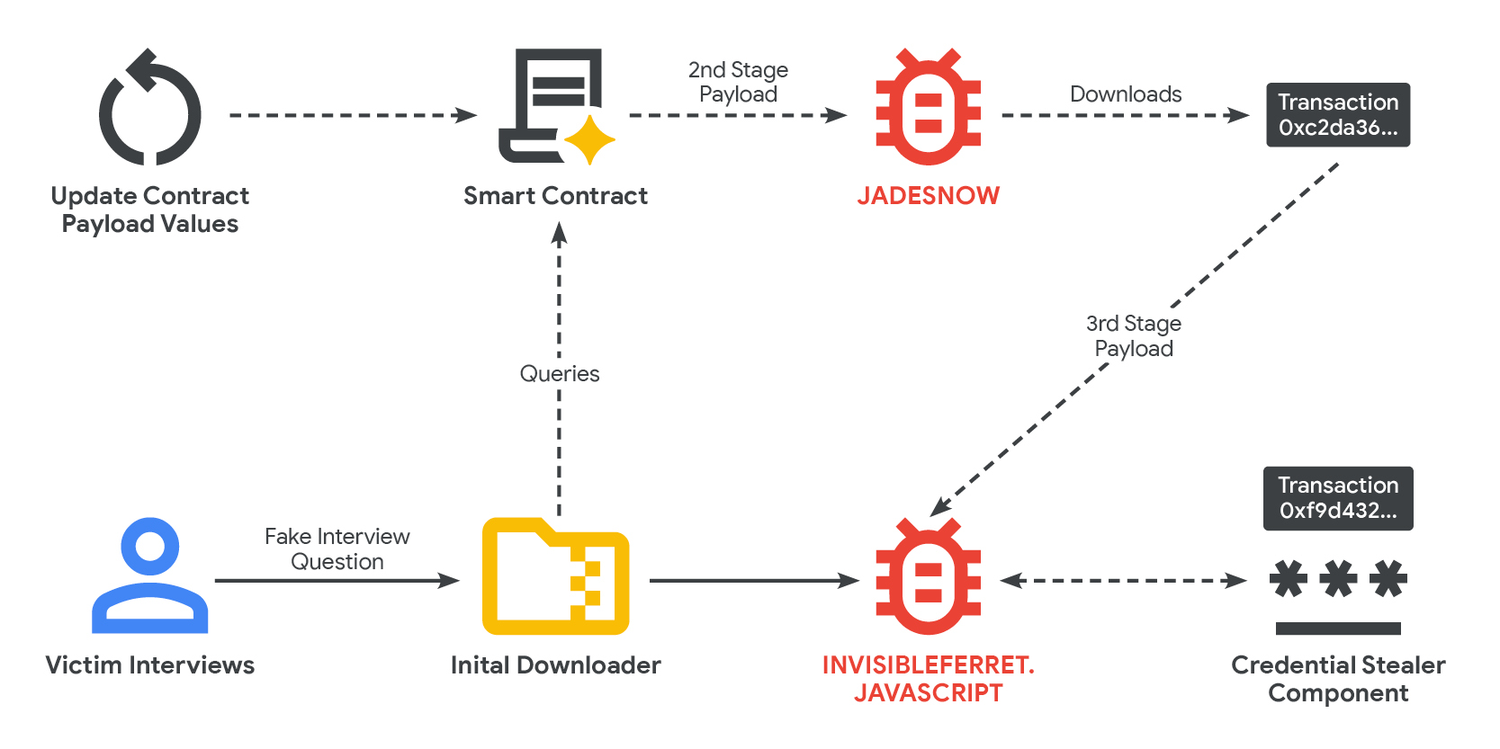
The process begins with the creation or modification of smart contracts,which surprisingly costs less than $2 per transaction. This affordability represents a significant advantage for attackers, reducing both the financial burden and the logistical complexity of deploying malware. Once established, these smart contracts act as repositories for malicious payloads.
Attackers are using social-engineering tactics, including fictitious job postings, to target individuals, particularly those involved in cryptocurrency application progress or other online services. Candidates are presented with coding or code-review challenges, and the malicious files are embedded within the materials required to complete these assessments.
North Korean Involvement
Security researchers have identified a North Korean-backed hacking group, designated UNC5342, as a primary user of this technique. This group employs earlier-stage malware, known as JadeSnow, to retrieve subsequent payloads directly from the Ethereum and BNB Smart Chain blockchains. What is particularly unusual is that UNC5342 is utilizing multiple blockchains. This suggests a possible division of labor within the group, with separate teams responsible for different aspects of the operation.
The versatility of EtherHiding allows for rapid updates to the infection chain and shifts in payload delivery locations.As a notable example, the JADESNOW downloader can seamlessly switch between fetching payloads from Ethereum or the BNB Smart Chain, potentially to take advantage of lower transaction fees on alternate networks.
Financial Motivation and Growing Sophistication
Beyond state-sponsored actors, financially motivated groups, such as UNC5142, are also observed leveraging EtherHiding.This demonstrates the widespread appeal of the technique across the cybercrime landscape. north Korea’s cyber capabilities have demonstrably improved over the last decade, with a series of increasingly enterprising and prosperous attacks. Elliptic, a blockchain analysis firm, recently reported that North Korea-linked hackers have stolen over $2 billion in cryptocurrency during 2025 alone.
| Threat Actor | Primary Motivation | Malware used | Blockchain(s) Utilized |
|---|---|---|---|
| UNC5342 | State-Sponsored (North Korea) | JadeSnow | Ethereum,BNB Smart Chain |
| UNC5142 | Financial Gain | Unspecified | Ethereum,BNB Smart Chain |
Did You Know? The low cost of smart contract transactions – frequently enough under $2 – makes blockchain-based malware delivery exceptionally accessible for attackers.
Pro Tip: Always exercise extreme caution when downloading files from unfamiliar sources, especially as part of a job application process.
As blockchain technology continues to evolve, so too will the tactics employed by malicious actors. Understanding these evolving threats is crucial for organizations and individuals alike to protect themselves from cyberattacks.
What steps do you think are most important for developers to take to defend against threats like EtherHiding? How can blockchain platforms improve security measures to prevent malicious use?
The Future of Blockchain Security
The emergence of EtherHiding underscores the evolving nature of cybersecurity threats and the need for continuous adaptation. As blockchain technology becomes more integrated into critical infrastructure and financial systems, securing these platforms will become paramount. Future developments are likely to include more sophisticated security protocols, enhanced monitoring tools, and increased collaboration between cybersecurity firms and blockchain developers.
Frequently Asked Questions About EtherHiding
- What is EtherHiding? EtherHiding is a new technique where malicious actors use blockchain smart contracts to store and deliver malware.
- Which blockchains are being targeted by EtherHiding? Currently, Ethereum and the BNB Smart Chain are the primary blockchains being exploited.
- How does EtherHiding work? attackers create smart contracts, then embed malicious code within files and distribute them, often through social engineering.
- Is North Korea involved in EtherHiding? Security researchers have linked a North Korean-backed hacking group, UNC5342, to the use of this technique.
- What is the cost of using etherhiding for attackers? Creating smart contracts is relatively inexpensive, costing less than $2 per transaction.
- How can I protect myself from EtherHiding? Exercise caution when downloading files from unfamiliar sources and be wary of suspicious job postings or coding challenges.
- What is the impact of EtherHiding on cybersecurity? EtherHiding introduces a new vector for malware delivery and requires increased vigilance from cybersecurity professionals.
Share this article and let us know your thoughts in the comments below!
