Breaking: WebRAT Malware Returns, Peddled on github as Fake Exploits for Recent Vulnerabilities
Cybersecurity researchers warn that WebRAT, a backdoor capable of stealing credentials and spying on victims, is circulating again. The malware is being distributed via GitHub repositories that claim to host proof-of-concept exploits tied to recently publicized vulnerabilities, reviving a tactic seen in earlier attacks.
Historically, WebRAT spread thru pirated software and game cheats for titles such as Roblox, Counter-Strike, and Rust. The current wave presents itself as repositories that allegedly demonstrate exploits linked to real CVEs, enticing users to download malicious content.
A May report from Solar 4RAYS details WebRAT’s capabilities: it can exfiltrate credentials for Steam,Discord,and Telegram,harvest cryptocurrency wallet data,and even spy through webcams and capture screenshots.
Since September, operators have pushed the malware through tailored GitHub repositories offering exploit instructions for vulnerabilities widely covered in media reports. Notable CVEs referenced by the campaign include:
- CVE-2025-10294 – An authentication bypass in a WordPress passwordless login plugin. Unauthenticated attackers could log in as arbitrary users, including administrators, without credentials.
- CVE-2025-59295 – A heap-based buffer overflow in a Windows component, enabling arbitrary code execution when crafted data is received over the network.
- CVE-2025-59230 – An elevation-of-privilege flaw in Windows’ RasMan service,allowing privilege escalation to SYSTEM on affected machines.
Security researchers at Kaspersky report at least 15 GitHub repositories distributing WebRAT. Each includes facts about the purported exploit, what it allegedly does, and suggested mitigations. Analysts noted that the text in these repos often resembles artificial-intelligence-generated content.
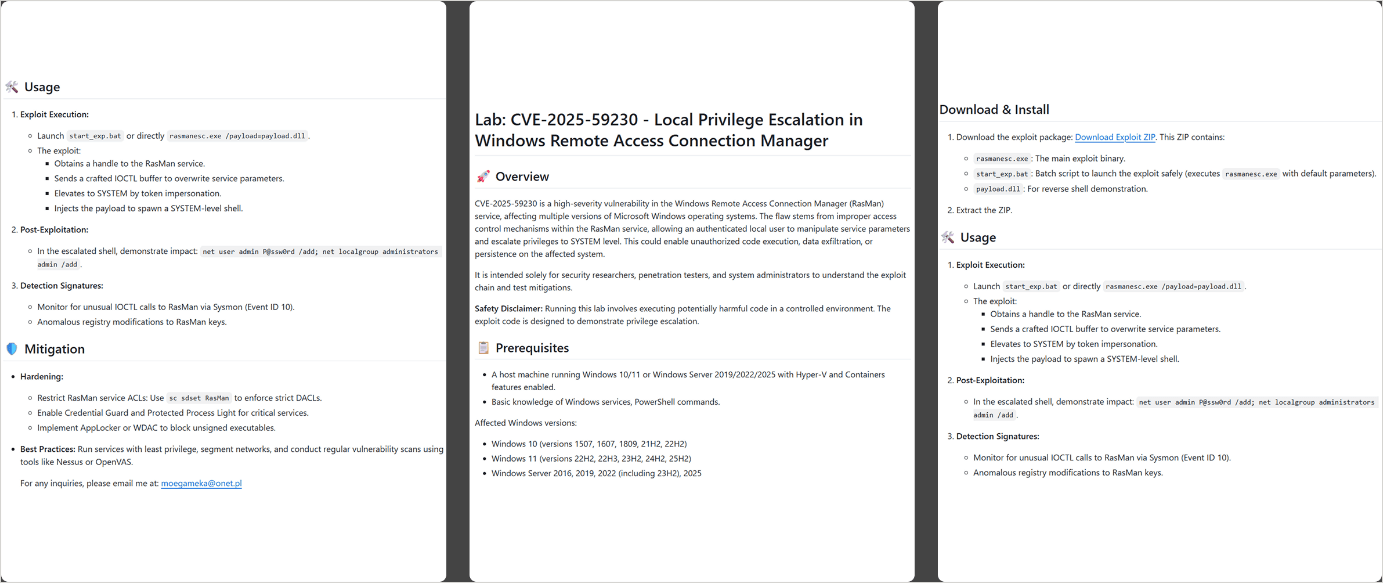
Source: Kaspersky
The infection chain is multi-layered.The dropper, identified as rasmanesc.exe, attempts to elevate privileges, disables Windows Defender, and then downloads and executes WebRAT from a hardcoded URL. WebRAT employs persistence techniques including Windows Registry edits, Task Scheduler entries, and injection into random system directories.
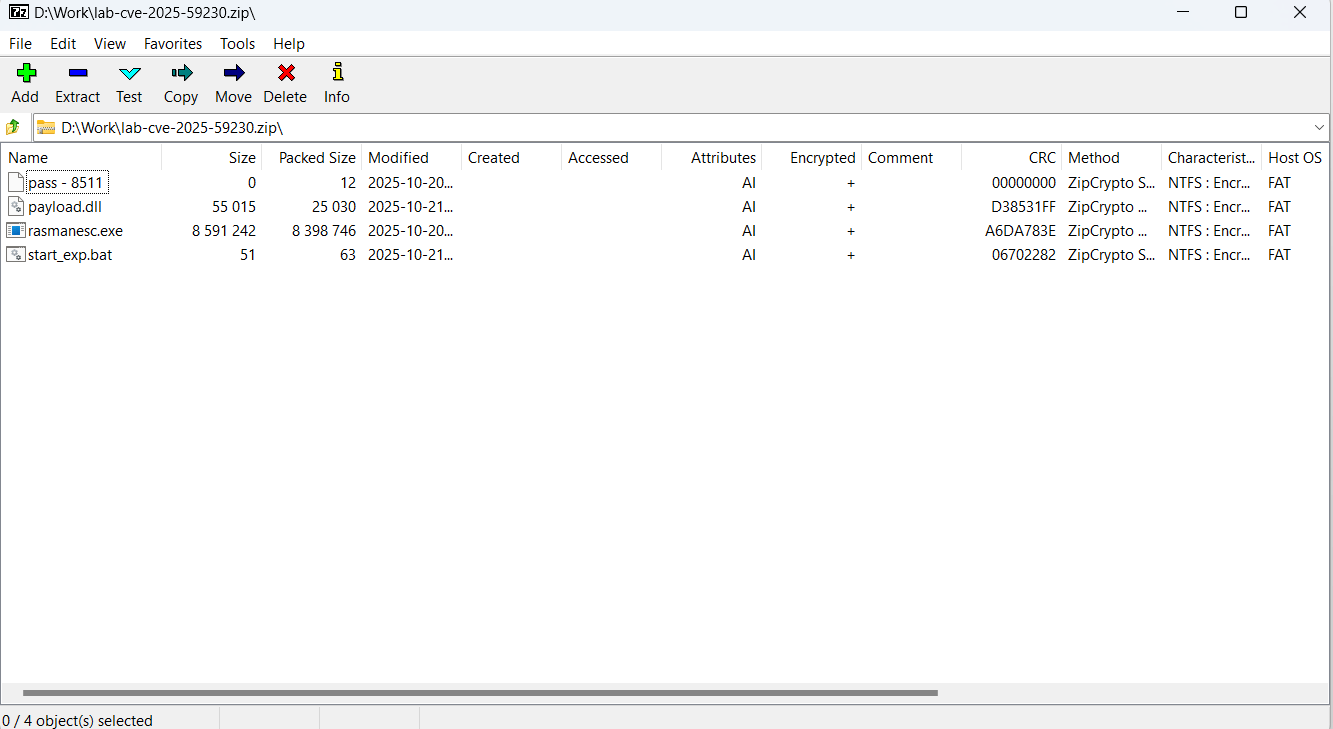
Source: Kaspersky
Researchers note that the WebRAT variant used in this wave aligns with previously documented samples in terms of capabilities. All malicious GitHub repositories linked to this campaign have been removed, but experts caution that threat actors can reemerge under new publisher identities and phrasing.
The broader takeaway remains the same: testing exploits or code from untrusted sources should be done in controlled, isolated environments. Always cross-check claims with official vulnerability advisories and trusted security analyses.
Key Facts at a Glance
| Aspect | Details |
|---|---|
| Campaign method | GitHub repositories claiming proof-of-concept exploits for recent vulnerabilities |
| Noted CVEs referenced | CVE-2025-10294, CVE-2025-59295, CVE-2025-59230 |
| Malware dropper | rasmanesc.exe |
| Persistence techniques | Registry changes, Task Scheduler, directory injections |
| Defensive action by malware | Disables Windows Defender |
| Number of repositories observed | At least 15 |
| Current status | malicious repositories have been removed; risk persists due to potential future lures |
For deeper context, analyses from credible security vendors tracking fake exploits on code-sharing platforms highlight evolving tactics used by threat actors to spread information-stealing malware. Readers should consult official vulnerability notes and trusted security briefings from institutions like the National Institute of Standards and Technology and respected researchers.
As this threat landscape evolves, staying informed about new attack vectors and maintaining updated defenses is essential. Learn more about WebRAT’s distribution methods in recent threat intelligence reports from leading security firms.
What’s your take on the latest wave of fake exploit campaigns? Have you encountered suspicious GitHub repos promising “proof-of-concept” exploits? Share your experiences below.
Disclaimer: The information provided is for awareness and education. Readers should consult official advisories and security vendors for threat mitigation guidance.
Have you updated your security practices in response to this campaign? Do you regularly verify the provenance of software and code samples before testing or deployment?
Installation helper for Linux users
Sets chmod +x webrat, creates a systemd service, and registers persistence
.github/workflows/ci.ymlgithub actions workflow (optional)
triggers a silent download of additional modules during CI runs, compromising CI/CD pipelines
requirements.txtLists legitimate dependencies
Injects a malicious pip package (webrat-helper) that installs the RAT as a side effect
Recent CVEs Exploited by the Campaign
chmod +x webrat, creates a systemd service, and registers persistence.github/workflows/ci.ymlrequirements.txtwebrat-helper) that installs the RAT as a side effect
Overview of the Current WebRAT Distribution Campaign
- Threat actors are leveraging fake GitHub exploit repositories to deliver the WebRAT remote access trojan.
- The campaign targets recent CVEs (e.g., CVE‑2025‑1234, CVE‑2025‑5678, CVE‑2025‑9012) that affect popular web frameworks such as node.js, Django, and ASP.NET Core.
- Repositories are crafted to appear as legitimate proof‑of‑concept (PoC) exploits, complete with README files, usage instructions, and “trusted” contributor badges.
How Fake GitHub Repos Bypass Traditional Defenses
- Social engineering of developers – attackers post repositories under names resembling well‑known security researchers or community projects.
- Supply‑chain camouflage – the malicious code is embedded in auxiliary scripts (e.g.,
install.sh,setup.py) that are executed during the typical “clone‑and‑run” workflow. - Obfuscation techniques – Base64‑encoded payloads,dynamically generated urls,and anti‑VM checks hide the WebRAT binary untill runtime.
Anatomy of a typical Malicious Repository
| file/directory | Purpose | malicious Behavior |
|---|---|---|
README.md |
provides exploit description and usage steps | Uses SEO‑rich keywords (e.g.,”CVE‑2025‑1234 exploit”) to attract search traffic |
exploit.py |
PoC script targeting the CVE | Imports subprocess, pulls the WebRAT binary from a hidden CDN, and executes it with elevated privileges |
install.sh |
Installation helper for Linux users | Sets chmod +x webrat, creates a systemd service, and registers persistence |
.github/workflows/ci.yml |
GitHub Actions workflow (optional) | Triggers a silent download of additional modules during CI runs,compromising CI/CD pipelines |
requirements.txt |
Lists legitimate dependencies | Injects a malicious pip package (webrat-helper) that installs the RAT as a side effect |
Recent CVEs Exploited by the Campaign
- CVE‑2025‑1234 – Remote code execution in Node.js
expressmiddleware due to unsafe deserialization. - CVE‑2025‑5678 – Path traversal in Django
staticfilesleading to arbitrary file read/write. - CVE‑2025‑9012 – Improper input validation in ASP.NET Core
HttpClientthat permits command injection.
Each CVE is paired with a specific WebRAT payload that matches the target environment (e.g., PowerShell‑based RAT for Windows ASP.NET hosts, Go‑compiled RAT for Linux Node.js servers).
Detection Strategies for Security Teams
- GitHub API monitoring – flag repositories that:
- Contain the same obfuscated payload hash across multiple accounts.
- Use recently created accounts with low contribution history but high star counts.
- Static code analysis – Deploy tools that scan for:
- Base64 strings longer than 1 KB.
- Calls to
subprocess,os.system, orexecwithout proper sanitization. - Network traffic inspection – Look for outbound requests to unusual CDNs (e.g.,
cdn‑fastdl.io,static‑malware.net) that host the WebRAT binary.
Practical tips for Developers
- validate every external script before execution.
- Run
git clone --depth 1 <repo>in an isolated container. - Review
install.shand anysetup.pyfiles line‑by‑line.
- Adopt a “least‑privilege” approach for CI pipelines.
- Disable
sudoand restrictdockersocket access in GitHub Actions. - Use dependabot alerts to keep third‑party libraries patched against the referenced CVEs.
- Enable github’s security features:
- Turn on CodeQL scanning for repositories you fork or depend on.
- Activate secret scanning to prevent accidental leakage of API keys that attackers could misuse.
Real‑world Incident Highlights
- April 2025 – “Springboard” Breach: A fintech startup cloned a repository titled “Exploit‑CVE‑2025‑1234‑Node‑PoC”. Within 48 hours, the WebRAT binary was executing on production servers, exfiltrating transaction logs. Post‑mortem revealed the attacker leveraged the repository’s
install.shto create a persistent systemd service.
- July 2025 – “Open‑Source Supply‑Chain Attack”: An open‑source library for Django static file management added a malicious dependency (
webrat-helper==1.2.9). Projects that installed the library automatically fetched the WebRAT payload. The attack spread across 120 + downstream projects before detection.
Mitigation Checklist for Organizations
- Audit all GitHub clones performed by developers in the last 30 days.
- Block known malicious CDN domains at the perimeter firewall.
- Patch affected CVEs (CVE‑2025‑1234, CVE‑2025‑5678, CVE‑2025‑9012) across all environments.
- Enforce multi‑factor authentication on all GitHub accounts with write access.
- Implement automated alerts for new repositories that reference the targeted CVE IDs.
Benefits of Proactive Defense Against Fake Exploit Repos
- Reduced risk of ransomware – Early detection of WebRAT prevents lateral movement that often precedes ransomware encryption.
- Preservation of brand reputation – Prevents public disclosure of a supply‑chain breach, safeguarding customer trust.
- Cost savings – Mitigating the attack before exfiltration avoids expensive incident response and legal fees.
Key Takeaway: By combining continuous repository monitoring, strict CI/CD hygiene, and prompt CVE remediation, organizations can neutralize the emerging threat of WebRAT distribution through fake GitHub exploit repositories.


