Google Apps Script Exploited in Wave of Sophisticated Phishing Attacks
Cybercriminals are increasingly leveraging the “Google Apps Script” advancement platform to craft highly convincing phishing scams designed to pilfer login credentials. This alarming trend involves hosting fraudulent login pages that appear legitimate, making it harder for users to discern the threat.
Security researchers at cofense have recently uncovered this tactic, warning that the fake login screens used in these attacks are meticulously designed to mimic genuine login interfaces, significantly increasing the risk of prosperous credential theft.
the mechanics of the Attack
“The attack begins with an email disguised as an invoice, complete with a link that directs the recipient to a webpage hosted on Google Apps Script,” Cofense researchers explained. This platform is integrated across google’s range of products. By hosting the phishing page within Google’s infrastructure, attackers exploit the inherent trust associated with Google domains.
This creates a deceptive habitat where unsuspecting users are more likely to hand over their sensitive information, believing they are interacting with a secure Google service. The attackers are banking on this trust to bypass typical security warnings and user skepticism.
Legitimate Service, Illegitimate use
Google Apps Script, a JavaScript-based cloud scripting platform, is designed to enable users to automate tasks and extend the functionality of Google Workspace applications such as Sheets, Docs, Drive, Gmail, and Calendar.
These scripts operate on the trusted Google domain “script.google.com,” which is often whitelisted by security products. Attackers exploit this trust by creating scripts that display fake login pages, capturing the credentials entered by victims. The stolen data is then discreetly transmitted to the attacker’s server through a hidden request.
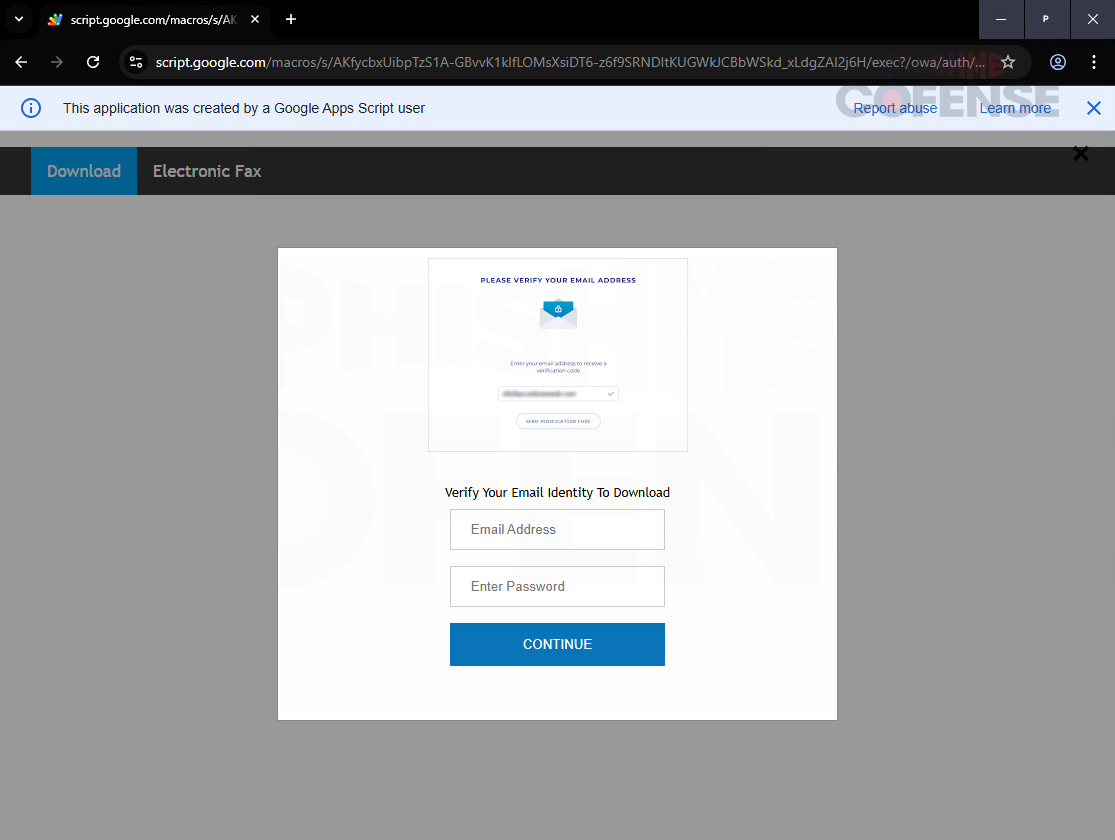
Source: Cofense
The ease with which anyone with a Google account can publish a script as a public web app, complete with a Google domain, allows threat actors to distribute these malicious links via phishing emails, often bypassing security alerts.
These emails typically feature a call to action related to invoice payments or tax matters, enticing recipients to click the link and unknowingly navigate to the Google-hosted phishing page.
.jpg)
Source: Cofense
once a victim enters their username and password, they are redirected to the legitimate service they intended to access. This redirection is a tactic used to reduce suspicion while providing the attackers with the necessary time to exploit the stolen credentials.
Did You Know? According to Verizon’s 2024 Data Breach Investigations Report, phishing is still one of the moast prevalent attack vectors, accounting for a significant percentage of data breaches. Always double-check before you click!
Defense Measures
The rising abuse of Google Apps Script in phishing campaigns highlights the necessity for robust security measures. One effective strategy involves configuring email security systems to thoroughly examine links to cloud services.
Ideally, organizations should block access to Google Apps Script URLs entirely or, at the very least, flag them as potentially dangerous, providing an extra layer of protection for their users.
Pro Tip: Enable multi-factor authentication (MFA) on all your accounts.Even if your credentials are stolen, MFA adds an extra layer of security by requiring a second verification method.
Key Takeaways: Google Apps script Phishing
| Aspect | Description |
|---|---|
| Attack Vector | Phishing emails containing links to malicious Google Apps Script webpages. |
| Exploited Service | Google Apps Script, a legitimate cloud scripting platform. |
| Objective | Steal user credentials by mimicking legitimate login pages. |
| Defense | Enhanced email security, scrutiny of cloud service links, user education. |
The Evergreen Threat of Phishing
Phishing remains a persistent and evolving threat, constantly adapting to new technologies and security measures. As attackers become more sophisticated, it’s crucial for individuals and organizations to stay informed and proactive in their defense strategies.
This includes continuous security awareness training, implementing advanced threat detection systems, and fostering a culture of vigilance. Regularly updating security protocols and staying abreast of the latest phishing techniques are also essential steps in mitigating the risks associated with these attacks.
What security measures do you find most effective in preventing phishing attacks? Have you ever been targeted by a phishing scam?
Frequently Asked Questions
-
What is Google Apps Script and why is it being used in phishing attacks?
Google Apps Script is a cloud scripting platform that allows users to automate tasks within Google Workspace. It’s being exploited in phishing attacks because scripts run on a trusted Google domain, making the phishing pages appear legitimate.
-
How can I identify a phishing email that uses Google Apps Script?
Look for emails containing links to Google Apps Script URLs (script.google.com) that request your login credentials. Be wary of unsolicited emails asking for immediate action, such as invoice payments.
-
What are the risks of falling victim to a Google Apps Script phishing attack?
If you enter your credentials on a fake login page, attackers can steal your username and password, potentially gaining access to your email, documents, and other sensitive information.
-
What steps can I take to protect myself from Google Apps script phishing scams?
configure your email security to scrutinize cloud service links. Consider blocking access to Google Apps Script urls or flagging them as potentially dangerous. Always verify the legitimacy of the sender before clicking any links or providing personal information.
-
Is Google taking any action to address the abuse of Google Apps Script for phishing?
while it’s unconfirmed if Google has specific plans, security professionals recommend implementing anti-abuse measures to detect and prevent the use of google Apps Script in phishing attacks.
-
Why are attackers increasingly using legitimate platforms like Google Apps Script for phishing?
Attackers use legitimate platforms to evade security measures and create an illusion of authenticity,making it easier to trick recipients into providing sensitive information. This also allows for more flexibility in adjusting the phishing script remotely.
Stay vigilant and share this article to help others stay safe from these evolving phishing tactics. Do you have any tips for spotting phishing attempts? Share your thoughts in the comments below!
