“`html
Serial Hacker ‘IntelBroker‘ Charged in $25 Million Cybercrime Spree
Table of Contents
- 1. Serial Hacker ‘IntelBroker’ Charged in $25 Million Cybercrime Spree
- 2. The Indictment Against Kai West
- 3. Notable Breaches Linked to IntelBroker
- 4. Legal Ramifications and Extradition
- 5. How The Fbi Unmasked Intelbroker
- 6. BreachForums Operators Also Apprehended
- 7. The Growing threat of Cybercrime
- 8. Key Facts About The Intelbroker Case
- 9. Staying Safe Online: Proactive Measures
- 10. Frequently Asked Questions (Faqs)
- 11. Here’s a PAA (People Also Ask) related question for the provided article, formatted on a new line:
- 12. IntelBroker: A Deep Dive into the Notorious Hacker and Global Data Breaches
- 13. Who is IntelBroker? unmasking a Threat Actor
- 14. IntelBroker’s Alleged Tactics and Methods
- 15. Notable Targets and Breaches Attributed to IntelBroker
- 16. Case Study: Hewlett-Packard Enterprise (HPE) Breach
- 17. The Impact of IntelBroker’s Activities
- 18. Impact on Businesses
- 19. Impact on Individuals
- 20. protecting Against Threats Like IntelBroker: Practical Tips
- 21. for Businesses: Best Practices
- 22. For Individuals: Personal Security Measures
New York,June 26,2025 – A British national,known online as “IntelBroker,” has been indicted in the U.S. for allegedly stealing and selling sensitive data, resulting in approximately $25 million in damages worldwide. The U.S. Attorney’s Office for the Southern District of New York announced the charges today.
The Indictment Against Kai West
Kai West, a 25-year-old British man, is accused of operating under the alias “IntelBroker” for years, illicitly obtaining and selling data from government entities, corporate networks, and critical infrastructure systems. The data was frequently enough offered for sale on the BreachForums hacking forum.
The stolen facts included sensitive health records, internal documents from telecommunications and cybersecurity firms, and user data from various online platforms.
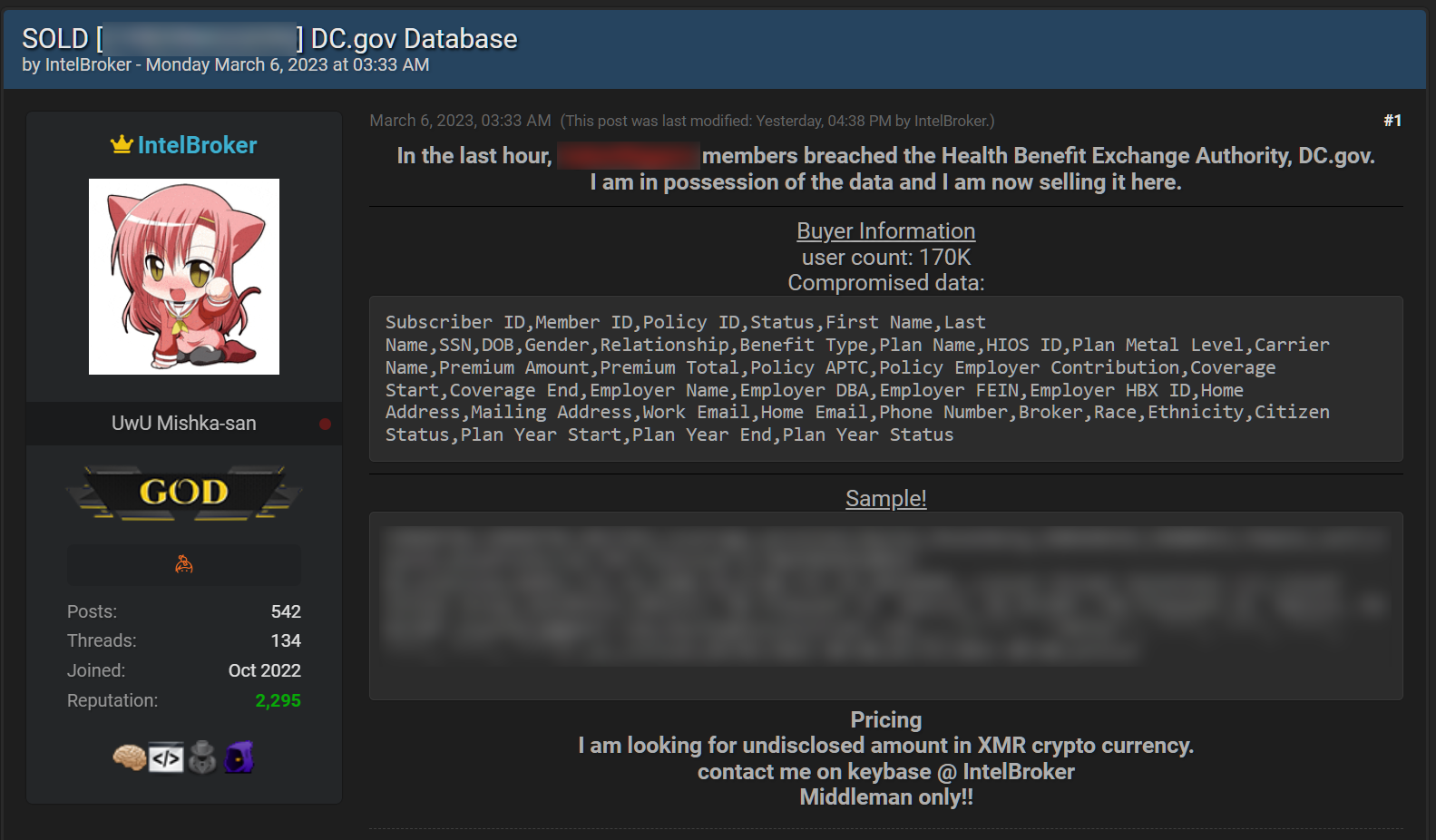
Notable Breaches Linked to IntelBroker
IntelBroker has been linked to several high-profile data breaches in recent years, including:
- Europol
- General Electric
- Weee!
- AMD
- HPE (Hewlett Packard Enterprise)
- Nokia
- DC Health Link
Legal Ramifications and Extradition
The four-count indictment includes charges of conspiracy to commit computer intrusions, wire fraud, conspiracy to commit wire fraud, and unauthorized access to a protected computer for information. if convicted, West could face a maximum penalty of 25 years in prison for three of the charges.
Authorities estimate that West’s activities caused approximately $25 million in damages to numerous victims.West was apprehended in France in February 2025, and the U.S.is currently seeking his extradition to face the charges in New York.
How The Fbi Unmasked Intelbroker
The examination revealed that an undercover agent purchased a stolen API key from IntelBroker in January 2023. The Bitcoin address used in the transaction was traced to a Ramp online banking platform account registered under West’s U.K. driving license.
The same email account was linked to a Coinbase account under the alias “Kyle Northern,” a known identity of West. This account contained invoices, university emails, and a photo of West’s license, solidifying the link between Kai West and the IntelBroker persona.
“The IntelBroker alias has caused millions in damages to victims around the world,” stated U.S. Attorney Jay Clayton.
The Fbi’s pursuit of cybercriminals remains unwavering, and New York is committed to bringing thes remote actors to justice.
BreachForums Operators Also Apprehended
In related news, four individuals believed to be the operators of the BreachForums hacking forums were also arrested in France this week.IntelBroker had previously served as an administrator for the forum before stepping down in January.
The Growing threat of Cybercrime
The arrest of “IntelBroker” highlights the increasing threat of cybercrime and the global efforts to combat it. Cybercrime continues to evolve, demanding heightened vigilance and robust security measures from individuals and organizations.
Did You Know? According to a recent report by Cybersecurity Ventures, global cybercrime costs are projected to reach $10.5 trillion annually by 2025, up from $3 trillion in 2015.
Key Facts About The Intelbroker Case
| Aspect | Details |
|---|---|
| Defendant | Kai West (aka “IntelBroker”) |
| Charges | Conspiracy to commit computer intrusions, wire fraud, etc. |
| Estimated Damages | $25 million |
| Arrest Location | France |
| Current Status | Awaiting extradition to the U.S. |
Staying Safe Online: Proactive Measures
Pro Tip: To mitigate the risk of data breaches, individuals and organizations should implement multi-factor authentication, regularly update software, and educate employees about phishing and other social engineering tactics.
- Regularly Update Software: Ensure all software and operating systems are updated with the latest security patches.
- Use Strong, Unique Passwords: implement a robust password policy and avoid reusing passwords across multiple accounts.
- Enable Multi-Factor Authentication (MFA): Add an extra layer of security by requiring a second verification method.
- Educate Yourself and Your Team: Stay informed about the latest cybersecurity threats and best practices.
- Monitor Your Accounts: Regularly check your financial and online accounts for any suspicious activity.
Frequently Asked Questions (Faqs)
