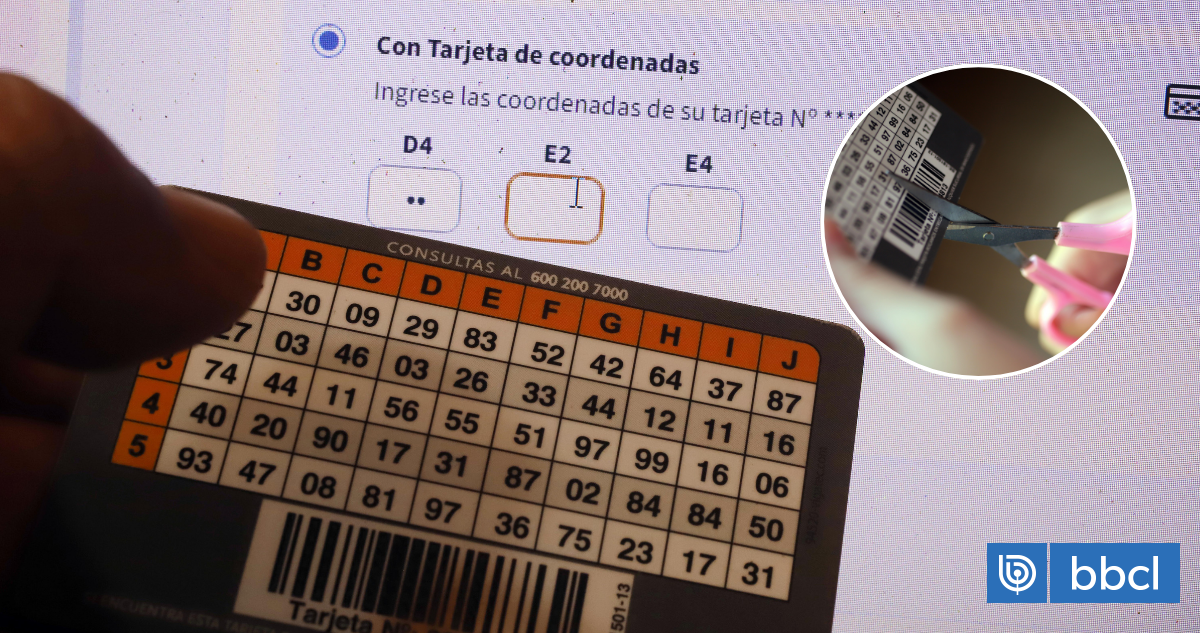
Chile’s Banking Shift: Why the End of Coordinate Cards Could Leave Millions Behind
Over 2.5 million Chileans still rely on coordinate cards – the plastic cards with grid-based security codes – to access their bank accounts. But that access is rapidly disappearing. This year marks the final phase-out, mandated by the Financial Market Commission (CMF), of these cards in favor of more modern authentication methods. While intended to bolster security, the transition is sparking concerns about financial exclusion, particularly for older adults and those with limited digital literacy.
The Push for Enhanced Security – and the Risks of Leaving People Behind
The CMF initiated the move away from coordinate cards last year, citing the need to strengthen banking authentication and combat rising fraud. The initial deadline of August 2023 was extended to August 2024 following significant backlash and warnings that a swift transition would disenfranchise vulnerable populations. Several banks, including Banco Estado, have already begun phasing out the cards for segments of their customer base, with further notices going out as recently as February 6th.
Economist Jean Paul Quinteros acknowledges the potential disruption but emphasizes the long-term benefits. “It’s important to raise the importance of greater security in the use of data to avoid possible scams or deception,” he stated. However, the core issue isn’t simply about security; it’s about digital inclusion. The shift demands a level of comfort with smartphones and online banking that isn’t universal.
A Generational Divide and the Threat of Financial Exclusion
Hernán Calderón, president of Conadecus, a consumer protection organization, is blunt: “This produces an exclusion from the financial system, mainly of people who are not digital natives… who do not have the expertise to be able to operate through a cell phone.” This isn’t hyperbole. For many older Chileans, the coordinate card represents a familiar and accessible way to manage their finances. Replacing it with biometric authentication, mobile apps, or even online passwords creates a significant barrier.
The problem extends beyond age. Individuals in rural areas with limited internet access, those with disabilities that hinder smartphone use, and those with lower levels of education are also at risk. The transition, without adequate support, could effectively lock these individuals out of essential financial services – from receiving pensions to paying bills.
Beyond the Card: The Future of Banking Authentication
The move away from coordinate cards is part of a broader global trend towards multi-factor authentication (MFA) and biometric security in banking. MFA combines something you know (a password), something you have (a smartphone), and something you are (a fingerprint or facial scan). Biometric authentication, in particular, is gaining traction due to its enhanced security and convenience. Javelin Strategy & Research highlights the increasing adoption of biometrics across financial institutions worldwide.
The Rise of Behavioral Biometrics
Looking ahead, we can expect to see even more sophisticated authentication methods emerge. Behavioral biometrics, for example, analyzes how a user interacts with their device – typing speed, mouse movements, scrolling patterns – to create a unique security profile. This offers a seamless and passive layer of security, reducing reliance on traditional passwords and PINs.
The Role of Voice Authentication
Another promising technology is voice authentication. Similar to facial recognition, voice authentication uses unique vocal characteristics to verify a user’s identity. This could be particularly beneficial for individuals who struggle with visual or physical impairments.
Bridging the Digital Divide: A Call for Proactive Solutions
The CMF’s initiative isn’t inherently flawed. Enhanced security is crucial in today’s digital landscape. However, the success of this transition hinges on proactive measures to mitigate the risk of financial exclusion. Eduardo Toro, executive director of Conecta Mayor UC, rightly points out that “improvements cannot be accompanied by restricting the autonomy in the use of the banking systems of each of the users.”
Banks need to invest in comprehensive digital literacy programs tailored to the needs of vulnerable populations. This includes providing accessible training, offering alternative authentication methods (perhaps a hybrid approach combining biometric and simpler options), and ensuring readily available customer support. Furthermore, government initiatives to expand internet access and digital infrastructure in underserved communities are essential.
The end of the coordinate card era is a pivotal moment for Chilean banking. It’s a test of whether innovation can truly benefit everyone, or if it will inadvertently create a two-tiered financial system. The answer will depend on a commitment to inclusivity and a willingness to prioritize the needs of those most at risk of being left behind. What steps do you think banks should take to ensure a smooth transition for all customers? Share your thoughts in the comments below!