atMicrosoft patched 128 security flaws on Tuesday (4/12)After that, information security practitioners jumped out to warn, among themCVE-2022-26809It is a zero-click vulnerability, and it is only a matter of time before an attack program appears, and it is bound to be patched first.
CVE-2022-26809Existing in the Remote Procedure Call (RPC) Runtime, as long as a hacker sends a specially crafted RPC call to the RPC host, it is possible to execute the program on the server with the RPC authority from the remote end, affecting all Windows and The Windows Server version has a CVSS risk score of up to 9.8. Microsoft recommends that enterprises close the perimeter firewall’s 445 TCP port to mitigate the vulnerability.
Information security industry Akamai pointed outCVE-2022-26809 is a zero-click vulnerability that requires no user interaction during mining, which increases the possibility of hackers eager to mine it, and any Windows device that exposes port 445 has associated risks. When queried with Shodan It was found that nearly 730,000 Windows devices worldwide exposed the port.
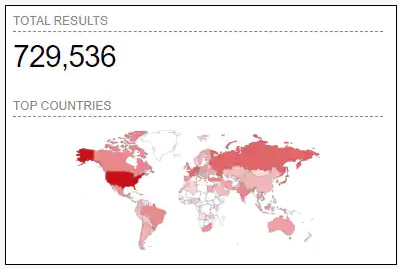
Image Source/Akamai
Since port 445 is usually used by Windows SMB,Another information security company Censys analysisAmong the more than 1.3 million machines that implement the SMB agreement worldwide, 63% use the Windows operating system, which is regarding 820,000. The top three markets with the most deployment are the United States, Russia and Hong Kong.
Hacker House co-founder Matthew Hickey《Bleeping Computer》He said that the vulnerability affects both the client and server-side PRC services. It is only a matter of time before hackers create the CVE-2022-26809 attack program, and it may bring serious consequences. Users should patch it as soon as possible.
